News tagged ‘exploit’
Unlock for iOS 4.1 and 4.2 is possible
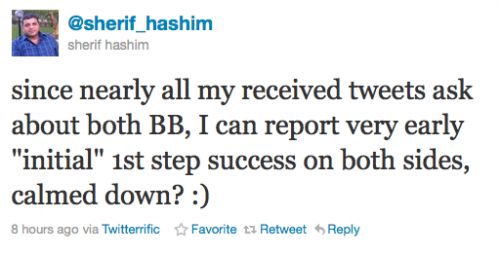
Hacker Sherif Hashim has discovered an exploit in iPhone's baseband which could bring an unlock for iOS 4.1 and iOS 4.2. Here are tweets from him:
@sherif_hashim: since nearly all my received tweets ask about both BB, I can report very early "initial" 1st step success on both sides, calmed down?

@sherif_hashim: @mrpauldurden a bit more sure than this, yeah
@mrpauldurden: @sherif_hashim very early first steps means.. you've found a crash that can potentially prove to be an expoitable vulnerability?
In the past Hashim found a baseband crash in iOS 4.0, his work brought us ultrasn0w 1.01, utility from DevTeam to unlock iPhone with iOS 4.0.
Another hacker Veeence tweets that the unlock won't be released till iOS 4.2. Apple plans to release 4.2 in November:
@veeence: A new exploitable baseband crash has been found. An unlock will very likely be released after iOS 4.2 and will unlock both BB's of 4.1 & 4.2
Step-by-step Tutorial: how to jailbreak iPad with iOS 3.2.2 using Limera1n (Windows)
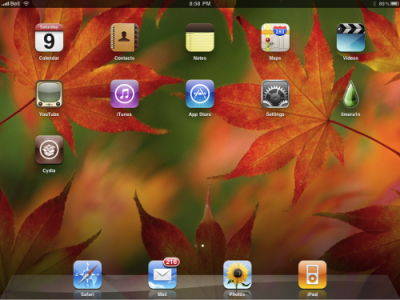
These are instructions on how to jailbreak your iPad with latest iOS 3.2.2 using Limera1n for Windows. You can find the Mac OS version of this tutorial here.
UPDATE: Please, consider reading our Jailbreak & Unlock FAQ, especially if you have questions or troubles.
Step 1
Open your browaer and navigate to and download LimeRa1n for Windows by clicking on the Windows.
When prompted save the download to your desktop
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Step-by-step Tutorial: how to jailbreak iOS 4.0-4.1 on iPhone 3GS or iPhone 4 using Limera1n (Windows)

These are instructions on how to jailbreak your iPhone 3GS (all bootroms) and iPhone 4 using Limera1n for Windows. Limera1n supports iOS 4.0, iOS 4.0.1, iOS 4.0.2 and iOS 4.1. Use the same steps to jailbreak iPod Touch 4G and iPod Touch 3G and even iPad. You can find the Mac OS version of this tutorial here.
Remember: Do not update to iOS 4.1 if you need the unlock. Ultrasn0w does not support that baseband yet.
UPDATE: Please, consider reading our Jailbreak & Unlock FAQ, especially if you have questions or troubles.
Step 1
Open your browaer and navigate to and download LimeRa1n for Windows by clicking on the Windows.
When prompted save the download to your desktop
 Leave a comment, read comments [141]
Leave a comment, read comments [141]
iPhone iOS 4.1 Jailbreak Released from GeoHot, called LimeRa1n

Famous hacker Geohot is back and today he released the latest iOS 4.1 jailbreak. It is called LimeRa1n and supports iPhone 3GS, iPod Touch 3G, iPad, iPhone 4, iPod Touch 4G with iOS firmwares 4.0-4.1 and beyond. It can also hacktivate your device, so there is no need in phone SIM-cards and other tricks.
This software is still in beta and was updated 3 times in last several hours. So use with caution.
There is Windows version only for now. Geohot plans to release LimeRa1n for Mac and Linux soon. You can Download it here.
Some users report that they have jailbroken their iOS 3.2.2 iPads successfully with limera1n, while others report that they tried, but failed.
Do not forget to backup.
For many users of iPhone 3GS and iPhone 4 with iOS 4.0.2 now there is a hope to perform jailbreak using LimeRa1n and unlock using ultrasn0w. We recommend NOT to do it if you have not saved your SHSH keys. You can try, but if something goes wrong without SHSH keys you'll have to restore to iOS 4.1, and there is no unlock for iOS 4.1 (possibly forever). Just wait for PwnageTool utility.
DevTeam reported that Limera1n uses a different exploit than SHAtter, so they will not release SHAtter utility, they don't want let Apple fix both security holes. However they plan to release PwnageTool using the same exploit.
You can find our LimeRa1n tutorials tutorials:
The Apple TV has just been jailbroken
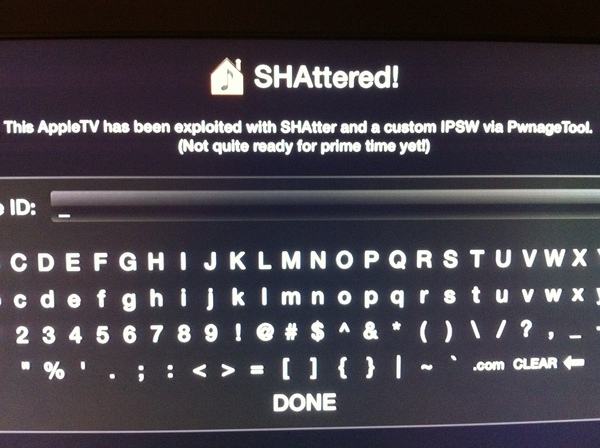
Today the new Apple TV has been jailbroken by hacker MuscleNerd from DevTeam. He used the SHAtter exploit. This means that hackers were able to gain full access to the device. Here is MuscleNerd's comment on twitter:
AppleTV 2G SHAttered and jailbroken (not quite sure how to run apps yet!)
MuscleNerd and the rest of the Dev-Team will probably create a public release of some utility soon. Here is a youtube video showing off the jailbroken device:
iPod Touch 4G with iOS 4.1 is jailbroken
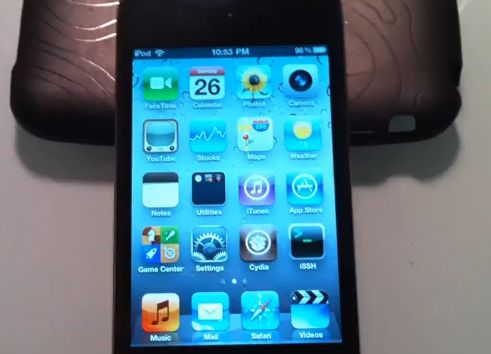
The new exploit is called SHAtter. It was developed by hacker pod2g a few months after hacker p0sixninja from the Chronic Dev Team discovered the crash. The same exploit can be used to jailbreak iPhone 4 and iPad with new firmwares. So iOS 4.1 and maybe even iOS 4.2 is not a problem any more. Soon we will see the utilities from DevTeam to perform the jailbreak.
The DevTeam published a video if a jailbroken iPod Touch 4G. Take a look:
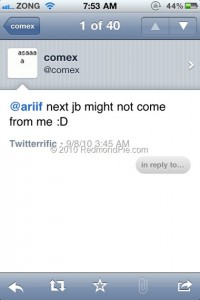
Comex Won't Release iOS 4.1 Jailbreak
Only a few days passed since Dev Team has confirmed that Comex will try to jailbreak iOS 4.1, using other exploit. However, according to the response received on Twitter, it became known that Comex may not take part in the new iOS 4.x jailbreak.
Comex replied to the message on Twitter in such a way: "ariif, the next jailbreak might not be from me ![]() ".
".
Of course, it does not mean that Comex leaves the scene and would not take part in jailbreaking as Geohot, most likely it is only this version he isn’t planning to jailbreak. Nevertheless the smile in his reply certainly means something good...
Jailbreak and Unlock for iOS 4.1 is possible

According to the latest tweets from different hackers (MuscleNerd, pod2g and others) the exploit for iOS 4.1 has been already discovered:
Works on 4.1 (!) iBSS iv=c2c5416472e5a0d6f0a25a123d5a2b1c key=1fbc7dcafaec21a150a51eb0eb99367550e24a077b128831b28c065e61f894a0
I just successfully updated to 4.1 without a baseband update. PLEASE wait for 4.1.0 TinyUmbrella!!!
Crazy timing that @pod2g got latest exploit just as 4.1 went public (lots of work left...keep away from 4.1 for now!)
congrats to @pod2g for the latest exploit and also @p0sixninja who have been trying for months.
This means that the jailbreak and unlock for iPhone and iPod Touch is possible. However please be patient and wait for the utilities.
Saurik released a PDF patch for older and already jailbroken iOS devices
As you may know, few days ago Apple had released a new version of iOS for all its mobile devices except first-generation iPhone and iPod touch, so owners of the latter are still not protected from a security flaw that allows hackers to obtain a remote control of their handsets. In fact, the latest compatible version for them is currently iOS 3.1.3.
But Saurik (who is known as a developer of Cydia) recently announced on the Dev-Team blog that he released a PDF patch that is compatible with any iOS version down to 2.x. It can be found in Cydia if you'll search for "PDF Patch". After installing it you can check if the patch is working properly with visiting jailbreakme.com page. After sliding the box to jailbreak you should only see the star background (and not a dialog box), which means you are no longer vulnerable.
Read the rest of this entry »
 Leave a comment, read comments [9]
Leave a comment, read comments [9]
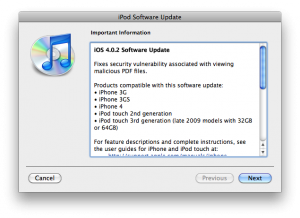
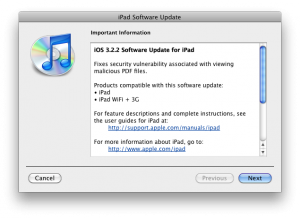
iOS 4.0.2 for iPhone, iOS 3.2.2 for iPad Have Been Released
Today Apple released patches for its iOS that address a security hole in Mobile Safari, which allowed users to jailbreak their iDevices. The PDF exploit they used also allowed hackers to gain remote control over the device with an iOS.
iOS 4.0.2 is available for:
- .
Apple did NOT release the patch for the first generation iPhones.
iOS 3.2.2 is intended to use on the .
You can update your device via the links above or simply by connecting your device to iTunes and clicking Update. But note, if you want to continue using jailbreak you should not update your handset/tablet and don't forget to backup your SHSH blobs.
Howto secure iPhone iOS: PDF exploit fix
There is a big a security hole in iPhone iOS. The device is insecure in a big and obvious way. You should be extremely careful of what sites you visit.
The FlateDecode vulnerability can be used when a PDF File is embedded within a Web page. Basically Safari tries to parse the PDF. And when it does it executes some code. Hackers can use this exploit to read and write iPhone data, get your contacts, sms, even delete something. So they can get all kinds to access your personal information stored on your iOS device.
Apple will fix it some day. Until then you need to take care of your iPhone security. There is a fix for that. It is available via Cydia for jailbroken devices. So you need to jailbreak in order to secure (funny isn't it?).