News tagged ‘security’
Apple television with 'iRing' accessory to launch this year
After meeting with Apple's suppliers in China, one analyst believes that Apple will release a TV with a new accessory that allows a user to control a TV using finger gestures.
Analyst Predicts Apple Will Launch iPhone 5S In June, Lower-Cost iPhone In September
Today Piper Jaffray analyst Gene Munster issued a new research note, predicting that Apple will launch an iPhone 5S in June and a lower-cost iPhone in September.
The iOS 6.1.3 Lock Screen Can Still Be Bypassed
Apple recently released iOS 6.1.3 which fixed a lock screen vulnerability; however, it turns out there is yet another one to be fixed.
As demonstrated in the video below, it's possible to get access to the Contacts app and then other areas of the phone including photos by using Voice Dial then ejecting the SIM card.
Sorry, iOS 6.1.3 has a new security flaw, but can be avoided easily. You should disable the "Voice Dial" option if you want to be safe.
Take a look...
Patent Holding Company Intertrust Files Patent Infringement Suit Against Apple
According to The Wall Street Journal, patent holding company Intertrust has filed a lawsuit against Apple, alleging that Cupertino-based company infringes on 15 of its patents. Intertrust licenses and invents technologies for digital rights management and currently holds more than 150 patents.
Apple fixed in iOS 6.1.3 four security issues used in Evasi0n
Apple has acknowledged the evad3rs for discovery of four of the six security issues fixed in iOS 6.1.3, notes MuscleNerd.
Apple gives hat tip to @evad3rs for 4 of the 6 security fixes in 6.1.3

dyld
Available for: iPhone 3GS and later, iPod touch (4th generation) and later, iPad 2 and later
Impact: A local user may be able to execute unsigned code
Description: A state management issue existed in the handling of Mach-O executable files with overlapping segments. This issue was addressed by refusing to load an executable with overlapping segments.
CVE-ID : CVE-2013-0977 : evad3rs
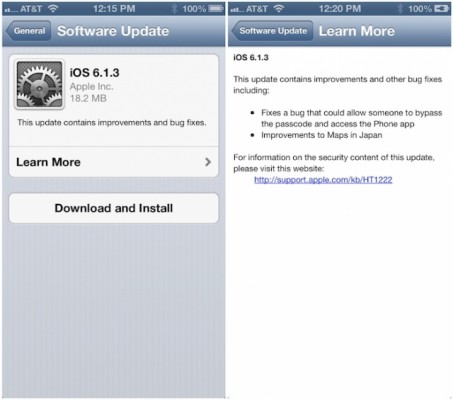
Apple Releases iOS 6.1.3 With Evasi0n Fix
Apple released iOS 6.1.3 which fixes a lock screen passcode bug and brings improvements to Maps in Japan. It also disables Evasi0n jailbreak.
iOS 6.1.3:
This update contains improvements and other bug fixes including:
● Fixes a bug that could allow someone to bypass the passcode and access the Phone app
● Improvements to Maps in JapanFor information on the security content of this update please visit this website:
You can update in iTunes or directly on your iDevice. If you use jailbreak or unlock, do not update! iOS 6.1.3 is not jailbreakable.
 Leave a comment, read comments [2]
Leave a comment, read comments [2]
iPhone 5S Will Include NFC Functionality And Fingerprint Sensor
China Times that Taiwanese chip company Chipbond has been chosen to supply a number of iPhone 5S’ components, including chips to support near field communication (NFC) functionality, fingerprint sensors and touch display drivers. According to the report, Apple will use the fingerprint sensor capabilities to improve the security of NFC-based features such as mobile payments.
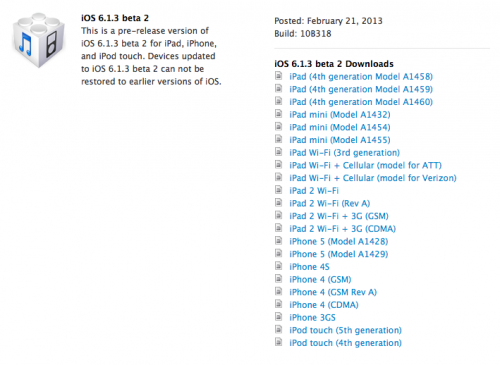
Apple Releases iOS 6.1.3 Beta 2 to Developers
Apple has released iOS 6.1.3 beta 2 to developers which includes a fix for the recently discovered lock screen bug.
iOS 6.1.3 Beta 2 includes a security fix for a Lock screen bug and the following improvements to Maps for Japan:
● Improved pronunciation of roads during turn-by-turn navigation
● Optimized directions to more strongly prefer highways over narrower roads
● Now indicates upcoming toll roads during turn-by-turn navigation
● Added labels for junctions, interchanges, on-ramps, off-ramps, and intersections
● Added indicators for transit station buildings, subway lines, and traffic lights
● Updated freeway color to green
● Updated icons for some location categories including fire stations, hospitals, and post offices
● Added 3D buildings including Tokyo Station, Japan Imperial Palace, and Tokyo Tower
You can get the new build (10B318) from the iOS Dev Center.
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Hackers Attacked And Infected A Number Of Apple Employees’ Macs
AllThingsD, Apple today confirmed that a number of Apple employees’ Macs were compromised by the same Chinese hackers, who recently targeted Facebook employees. The malware infected the computers through a vulnerability in a Java plug-in, which Apple has recently blocked due to security vulnerabilities. in statement to AllThingsD, Apple said:
iOS 6.1.1 beta does not fix latest evasi0n jailbreak
This is pretty interesting. Pod2g just announced that the new iOS 6.1.1 beta that Apple seeded to developers yesterday does not actually patch the exploits used in the latest jailbreak.
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Apple Posts Document Warning Users Against Jailbreaking
Apple has a document warning users that jailbreaking their iOS devices may cause instability, security vulnerabilities, shortened battery life, and other issues. The document was posted on February 3rd, the same day the Evasi0n jailbreak was originally expected to drop. Take a look:
 Leave a comment, read comments [3]
Leave a comment, read comments [3]
Untethered Jailbreak for iOS 6.0 and iOS 6.1b4 is Ready
Pod2g confirmed that the Evad3rs Dev-Team is ready with a jailbreak for iOS 6.1 and credits Planetbeing and Pimskeks for the accomplishment in an interview with iDigitalTimes.
"For your information and this is important to me that everybody knows about it also, this jailbreak will be @planetbeing and @pimskeks. I arrived at the end, gave ideas that pushed them to their maximum, I kinda unblocked the situation, but it would certainly have happened without me helping."
 Leave a comment, read comments [2]
Leave a comment, read comments [2]
The culprit that robbed Steve Jobs' family home, was sentenced to seven years in prison
IDG News Service reports that Kariem McFarlin, the robber who stole Apple products and other items of equivalent value at $ 60.000 from the home of Steve Jobs' family in last July, has been sentenced to seven years in prison. McFarlin broke into the house, which was in repairing, and stole two iMacs, three iPads, three iPods, Apple TV, jewelry and other items.
Oracle Released Java 7 Update 11 To Fix Security Vulnerability
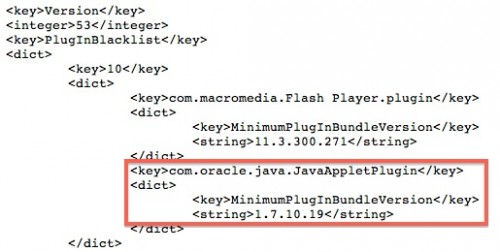
On Friday, we reported that Apple had used its anti-malware system in OS X in order to disable Java 7 browser plug-in over a security vulnerability that was widely exploited in the wild.
Apple's anti-malware tool is able to enforce minimum version numbers for such plug-ins as Flash and Java, and the company simply updated its blacklist to require that computers be running higher version of Java 7 than was publicly available.
Apple Disables Java 7 Plug-in On OS X To Address Security Threat
ZDNet, a in Java 7 has been discovered and is currently being exploited by malicious parties. The U.S. Department of Homeland Security recommended that users should disable the Java 7 browser plug-in until a patch is issued by Oracle. The report said: