News tagged ‘XEMN’
GeoHot and DevTeam discuss exploits for new firmware 3.1.3 baseband

A few days ago in an IRC channel the DevTeam and GeoHot discussed and summarized the state of the exploits found in the new baseband 05.12.01 in firmware 3.1.3. GeoHot explains that an exploit that had previously discovered and used in blacksn0w is still present in the new firmware released by Apple. It appears that both he and MuscleNerd are working on the same exploit, and if this were true, it would be a really good start to team up and release a new unlock tool.
Here is their discussion:
< visnet_ > What does geohot tweet mean?
< %geohot > its my bb exploit for safekeeping
< %Par4doX > geohot: did you turn that over to the dev team or are you doing something with it?
< %geohot > my days of turning things over are done
< %geohot > i hope its different from the one they have
< %geohot > but they prob already have it
< %geohot > its the one i orig wanted to release blacksn0w with
< %Par4doX > it’s still there in the new bb
< %geohot > yep, just checked
< %geohot > but then opted to use xemn since it was public
< Evan > Oo, it carries over from 05.11 to 05.12?
< %geohot > why wouldn’t it, apple doesn’t fix things proactivly
< @MuscleNerd > geohot we prob should figure out a way to know if we have same exploit double blind, otherwise we may release 2 different ones at same time
< %geohot > any suggestions?
< @MuscleNerd > not sure how to do that without making it easy to brute force tho
< %geohot > yea, i salted the hash
< @MuscleNerd > yeah
< @MuscleNerd > hmm maybe if we both hash the stack dump
< @Confucious > Can you two take this out of public sight?
< @MuscleNerd > the stack itself, not the header before it or the registers after it
< Her > muscle: any notice about the exploits are the same ?
< %geohot > we are working on it
< %geohot > cryptography, perfect for people who don’t trust each other
We should not expect much for the firmware 3.1.3 since the rumors predict the firmware 3.2 for mid-March. However these news are really good for owners of locked devices.
Apple Bans Hackers from iTunes App Store
It looks like Apple has started banning iPhone hackers from the iTunes App Store.
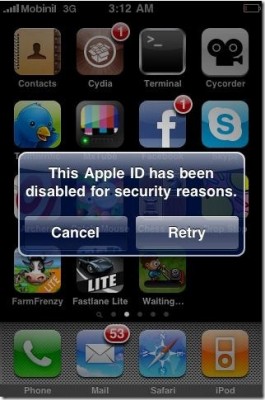
A few day ago Sherif Hashim, the iPhone developer and hacker, tweeted that he had found an exploit in the latest iPhone OS 3.1.3, which could enable the unlock on 05.12.01 baseband for iPhone 3GS and iPhone 3G. Yesterday he has been banned by Apple for the so called "security reasons". It seems that Apple is quite angry! Here is what Sherif gets when he tries to access App Store from his iPhone:
Sherif Hashim’s Tweets:
"Your Apple ID was banned for security reasons", that's what i get when i try to go to the app store, they must be really angry
))))
and guess what my apple ID was, "sherif_hashim@yahoo.com", what a fool was me not to notice
)), can't help laughing, they are babies
))
Another iPhone hacker named iH8sn0w, the developer of Sn0wbreeze (PwnageTool alternative for Windows), tweeted saying he was also banned by Apple right after he released an exploit known as XEMN:
@sherif_hashim lol, they did that to my ih8sn0wyday[@t]googmail.com too. (right after I posted XEMN)…
For now Apple isn’t banning Jailbreakers - they’re banning people who actively work to find exploits in the iPhone software to create Jailbreaks for the rest of us.
 Leave a comment
Leave a comment