News tagged ‘security’
Geohot Arrested for Marijuana Possession En Route to SXSW
Famous hacker George Hotz (aka Geohot) was arrested and charged with felony marijuana possession while en route to SXSW conference.
Hotz was on his way to give a talk at SXSW, when he had to pass through a border patrol checkpoint in Sierra Blanca. According to a source familiar with the case, Department of Homeland Security officers brought drug dogs to each car. When the dogs barked, Hotz (and his passengers) were pulled over for more searching.
Apple introduces Developer ID

On Monday Apple sent out e-mails inviting developers to prepare their software for OS X Mountain Lion by joining the Developer ID program. The program will allow for apps to run on a Mac or iOS device that is protected by the Gatekeeper anti-malware system that requires that apps be certified through the Developer ID program to ensure seamless installation.
Gatekeeper is a new anti-malware feature that, according to Apple, will filter out malicious third-party applications and prevent OS X users from "unknowingly downloading and installing malicious software." To that end, the system implements a hierarchy of security that is based on digital certificates embedded in a software's code.
Apple rumored to be secretly shipping 'iPad 3' as Best Buy cuts iPad 2 by $50
Meijer, a regional big-box retailer in the U.S., slashed the price of the 16GB iPad 2 with Wi-Fi by $70, and Best Buy has begun offering $50 off every iPad 2 model. These facts could, however, suggest that Foxconn is already preparing to ship the device's third-generation successor to Apple in the United States.
The alleged secret shipments from Foxconn were revealed in a shipping manifest from Apple.pro revealed this weekend, which shows a series of shipments scheduled to begin delivery in the U.S. no later than March 9. The mystery orders arriving from Chengdu, China, are said to be under high security. A source from Foxconn's Chengdu plant reportedly indicated that the shipment is for "Apple's latest products."
Foxconn's Servers Hacked, Exposing Vendor Usernames and Passwords
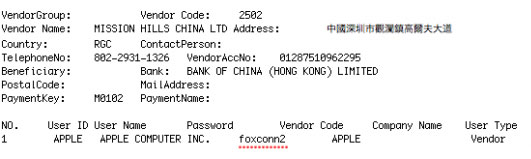
Swagg Security hacking group announced this week that they managed to hack Foxconn servers that expose usernames and passwords for clients and employees. Such information could be used to place fraudulent orders for companies like Apple and Microsoft.
Swagg Security alleged that it had bypassed Foxconn's firewall "almost flawlessly." Using several hacking techniques and a couple of days time, the hackers reportedly dumped "most of everything of significance," including usernames and passwords. According to the group, the leaked passwords "could allow individuals to make fraudulent orders under big companies like Microsoft, Apple, IBM, Intel, and Dell."
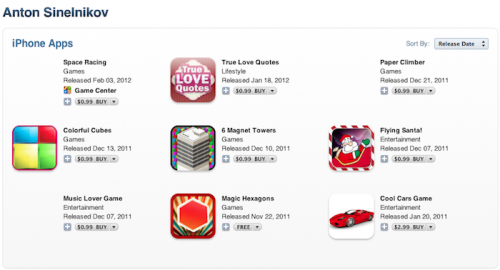
Apple removes blatant copycat apps from App Store
TechCrunch reports that Apple removed from the App Store a number of copycat applications such as Temple Run, Tiny Wings and Words with Friends that closely mimicked the titles of successful games after they provoked a public outcry from developers over the issue. The fraudulent apps were largely the work of developer Anton Sinelnikov.
Sinelnikov, however, is not alone in his efforts, as dozens of other applications from other developers have attempted to dishonestly capitalize on the successes of others. Numerous developers and users asked Apple to take down the offending apps. Keith Shepherd, the creator of Temple Run, noted on his account that an app like Temple Jump "taints the integrity of the App Store." After Apple pulled the app, Shepherd posted on Twitter that he was "thankful."
Taiwanese Site Sued by Supplier After Leaking Claimed iPad 3 Dock Connector

In July 2011 Taiwanese site Apple.pro published several photos of what was claimed to be the dock connector and ribbon cable for the next-generation iPad 3. Honestly, the connector didn’t provide much information about the full iPad 3 tablet. The only obvious fact was that the connector itself being white as opposed to black on the iPad 2, and it was one of the first reported leaks of iPad 3 parts. However, Apple's suppliers seem to have taken the leak seriously. Apple.pro now reports that it has been sued by the supplier responsible for the part leaked in last year's report.
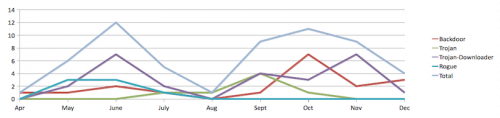
Mac platform faced 58 malware threats from Q2 to Q4 2011
Security lab F-Secure released its 2011 Mac Malware Summary earlier this week, noting that Mac OS X platform endured 58 separate malware attacks from April 2011 to December 2011. Of course, this numbers couldn’t be compared with multiply attacks that Microsoft's Windows operating system experienced over the same period.
The firm counted only unique variants of malware that occurred during the second, third and fourth quarters of 2011. "We prefer a more conservative approach when counting malware. The more generic and family based, the better," the report noted.
iOS Accessories At CES 2012: Wireless HDMI, Multi-docks, iNotebook, Kiosk
There are tons of accessories showed off at CES 2012, many of which were designed for iOS devices. Among the most interesting are multi-docs which offer various ways of charging several iOS devices simultaneously.
"Dream Team" will work on untethered iPad 2 and iPhone 4S jailbreak

Pod2g has recently announced that Planetbeing, MuscleNerd, and P0sixninja have joined his effort to release an iOS 5.0.1 untethered jailbreak for the iPhone 4S and iPad 2.
@planetbeing, the legendary hacker behind iPhone Linux and lot of jailbreaks has joined the A5 research! The famous @MuscleNerd, the leader of the iPhone Dev Team, who did a lot of tests for Corona and whom integrated it and made it simple in redsn0w is willing to help also. And last, but not least @p0sixninja, the leader of the Chronic Dev Team, and my partner for years on iPhone security research has started to code and fuzz the Apple sandbox.
That means that we now have a dream team to create a public release of the A5 jailbreak.
 Leave a comment, read comments [7]
Leave a comment, read comments [7]
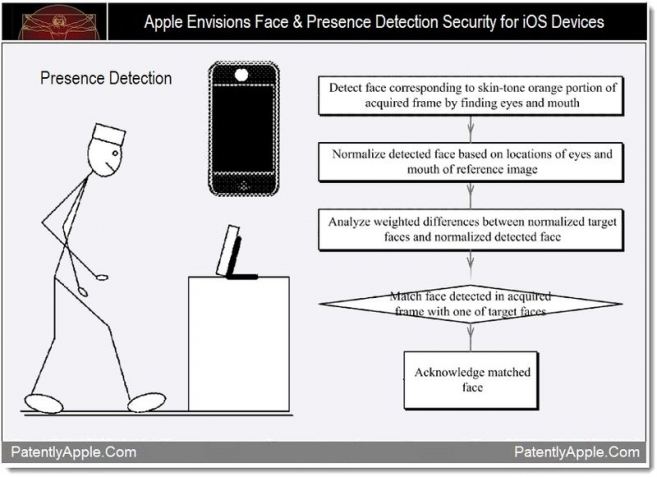
Apple Patent Describes Multi-User Face Detection System
Like the controversial face unlock functionality in Google’s Galaxy Nexus, a new Apple’s patent application points out that the company is developing similar but more sofisticated face detection solution. As PatentlyApple reports, Apple said that these user detection system could be included in a future MacBook, iPad, iPod touch and iPhone.
Read the rest of this entry »
Apple to Build Semiconductor R&D Center in Israel

The resent rumors suggesting that Apple may purchase Israeli firm Anobit, nudge that Apple plans to set up its first research and development center outside of its Cupertino headquarters.
Sources inform "Globes" that Apple Inc. has decided to open a development center in Israel focusing on semiconductors. The decision was taken even before the company entered into talks to acquire Herzliya-based flash storage solutions provider Anobit Ltd..
Apple has hired Aharon Aharon, a veteran player in Israel's high tech industry, to lead the new development center.
[...]
Developers crack Siri’s security protocol to enable it with any device
![]()
A team of developers called Applidium has announced that they managed to investigate how Siri, exclusive service available on the iPhone 4S, talks to Apple servers. Applidium notes that iPhone 4S uses standard HTTPS network requests to communicate with Apple's servers, but sends data using an "ACE" command rather than regular web GET requests. Moreover, each Siri request involves a unique identifier based on UUID. Such identifier prevents access of unauthorized devices to Apple’s servers. User’s requests are compressed with the Speex audio codec optimized for VoIP. Applidium discovered that iPhone, to provide Siri’s voice recognition, should support at least Siri's basic voice recognition features, but Apple doesn’t plan to port such capabilities on earlier iOS 5 models.
So far, Applidium's investigation has revealed that Siri packages requests in compressed property lists, but further exploration of the protocol is hampered by a number of issues, including the complexity of requests, the fact that they are tied to a hardware key, and that they are subject to change.
Noteworthy, Apple could at any time stop supporting a particular hardware identifier, if it is suspected of being used to exploit its servers, and change way of data transmitting.
Applidium says "anyone could now write an Android app that uses the real Siri! Or use Siri on an iPad!" But you will need a real unique user key of an actual iPhone 4S.
Jailbreakers and unlockers: don't update to iOS 5.0.1
Apple has recently released iOS 5.0.1. It is still tethered jailbreakable. However if you want untethered jailbreak or unlock - you should stay away from 5.0.1
Earlier this week pod2g reported that a code signing bug found in iOS 5.0 will make it easier for hackers to develop a full jailbreak for iOS 5 firmware version. That bug might have been closed in iOS 5.0.1. UPDATE: According to pod2g the bug is still present, but harder to exploit because another exploit found by Charlie Miller is fixed in iOS 5.0.1.
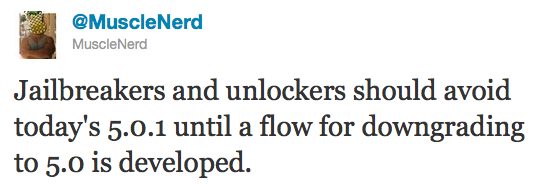
Also, MuscleNerd via twitter has warned iOS users that there is no downgrade from iOS 5.0.1 to iOS 5.0 yet and he recommends to wait until downgrade mechanism is available.
Jailbreakers and unlockers should avoid today's 5.0.1 until a flow for downgrading to 5.0 is developed.
Downgrade flow needs to be modified for AP "nonce" http://is.gd/b3G0io ... saved SHSH blobs are not enough to downgrade to 5.0
Apple Releases iOS 5.0.1 to Address Battery Life Issues
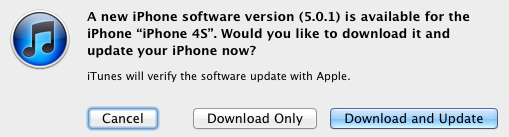
Yesterday Apple released the promised update of the iOS 5.0. The iOS 5.0.1 should fix battery life issues found on devices upgraded to the iOS 5, as well as on new iPhone 4S. Apple publicly said the battery life bugs affected a small number of users. In addition to addressing battery life issues, the update also brings new multi-touch gestures for the first-generation iPad.
This update contains improvements and other bug fixes including:
- Fixes bugs affecting battery life
- Adds Multitasking Gestures for original iPad
- Resolves bugs with Documents in the Cloud
- Improves voice recognition for Australian users using dictation
The update also includes security improvements, as well as a new way for developers to specify files that should remain on a device even in low storage situations.
iOS 5.0.1 is available for iPhone (4S, 4, and 3GS), iPod touch (third- and fourth-generation), and all iPad models. The update is now available to all users through iTunes, and will be soon available as an over-the-air update.
Direct links for downloads:
- iPhone: , , ,
- iPad: , , ,
- iPod touch: ,
iOS Security Exploit Allows Apps To Execute Malicious Code
Video where Miller demonstates this exploit
According to , security specialist Charlie Miller has found an exploit on iOS devices, which allows developers to put malware apps onto the App Store without detection. These malware apps can be used to steal user’s contacts, photo and other information, play a ringtone, make the device vibrate and more at any time the developer chooses.