News tagged ‘security’
18.6% Of Apps Collect User’s Address Book Data And 41% Track Location
Today security company BitDefender published a report (via ) that highlights the importance of adopting Apple’s data isolation policy in iOS 6.
Starting with the iOS 6 release this fall, apps that need access to personal data (reminders, photos, contacts, calendars etc.) will have to ask users to allow them use such data. However, according to BitDefender, now about 18.6% of 65,000 apps for iPhone that was included in the study can access data in a user’s address book, while 41% of them can track location. The company also revealed that only 57.7% of apps encrypt user’s personal data.
Apple Is Trying To Combat In App Purchase Hack
Last week we reported that Russian hacker has launched a new method allowing users of App Store to bypass In App Purchase system and obtain paid-in content for free. We also noted that apart from theft of content from developers the method exposed users of iOS devices to risks as their personal information was sent to hacker’s servers.
Now The Next Web issued a outlining some of the actions Apple has been taking to address the problem.
Apple Has Removed SMS Spam Application From App Store
Today Russian security company Kaspersky Lab that they had been notified about an app available in Google Play store (for Android) and Apple’s App Store that was quietly gathering data from user’s address book and sending it to the remote servers. Then the developer’s servers were sending SMS spam messages to contacts from the address book advertising the app, with the “From” field being filled with the mobile phone number of the original user.
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Step-by-step Tutorial: How to сreate an App Store account without a credit card on your iPhone, iPod Touch or iPad
This step-by-step tutorial will guide you through the process of creating Apple ID without using your credit card right on your iPhone, iPod Touch or iPad. This Apple ID is necessary to get free applications from AppStore.
- Open the App Store on your device.
- Find a free application on the App Store.
- Important: Before proceeding to the next step, you must download and install the free application by tapping Free followed by tapping Install.
Read the rest of this entry »
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Apple released iOS 6.0 Beta 2 for developers
Apple recently released new iOS 6 beta 2 for developers. It is available as an OTA update or as a download here. Apple also updated Xcode 4.5 developer preview 2, Apple TV beta 2 as well.
When you download and install iOS 6.0 Beta 2 OTA the Settings icon animates. Take a look:
Video of the Absinthe 2.0 Jailbreak announcement at HITB
Take a look at the video from RedmondPie of the Chronic Dev-Team announcing Absinthe 2.0 at HITB:
For those who didn't follow the conference, or get caught up in the excitement that surrounded it, the 'one more thing' bomb-shell was related to the fact that the Dream Team used their presence at the security event to officially introduce the world to the v2.0 release of their one-click Absinthe jailbreak solution. After months of hard work and exploit finding, mixed with weeks of will-they-won't-they speculation, it turns out that they indeed did introduce us to Absinthe 2.0.
Our instructions how to jailbreak your device using Absinthe are available here.
Here is the video:
More video:
Tim Cook says Apple is 'very serious' about doubling down on secrecy
Apple's secrecy surrounding its product line is legendary. Apple cofounder Steve Jobs even identified secrecy as one of the specific tenets at Apple that has been responsible for its success. And now Apple plans to become even more protective going forward, the company's chief executive said in an interview to the All Things D.
Questioned by journalists Kara Swisher and Walt Mossberg, Cook revealed that Apple plans to "double down" on product security and secrecy. "We're going to double down on secrecy," Cook said Tuesday. "I'm very serious about this. Double down."
How to backup your SHSH blobs using TinyUmbrella for Windows

Every time Apple releases a new firmware it stops the ability to restore to an older firmware. If you need to restore to old firmware you need to save your SHSH keys as soon as possible.
Here are instructions on how to backup your SHSH blobs using TinyUmbrella utility for Windows.
Step One
Download the latest version of TinyUmbrella from to your Desktop.
 Leave a comment, read comments [59]
Leave a comment, read comments [59]
Apple plans to block competitors' prying ears with new off-campus cafeteria
The San Jose Mercury News reports that on Tuesday the Planning Commission unanimously approved the project of 21,468-square-foot cafeteria near Apple’s Cupertino, Calif., headquarters. The non-Apple employees will not be welcomed in the cafeteria that will allow Apple employees to speak freely about their business without fearing that competitors are eavesdropping.
"We like to provide a level of security so that people and employees can feel comfortable talking about their business, their research and whatever project they're engineering without fear of competition soft of overhearing their conversations," said Dan Wisenhunt, Apple's director of real estate facilities. "That is a real issue today in Cupertino because we've got other companies here in our same business."
The cafeteria will be a two-story building that will include a cafe, meeting rooms, lounge areas and courtyard space. The second floor will be intended for cafeteria employees for storage, locker rooms, restrooms and more. The site will also include 70 parking spaces housed in an underground garage.
One more step towards untethered iOS 5.1 jailbreak
Pod2g has bypassed ASLR at bootup, making progress towards the public release of an iOS 5.1 jailbreak. ASLR is a security method that randomly arranges important data areas. This is one more step toward untethered iOS 5.1 jailbreak for all devices including iPhone 4S, iPad 2 and new iPad 3.
ASLR seems bypassed! Weird machines FTW. Time to ROP the payload.
Earlier this week pod2g revealed that the Chronic Dev-Team now has all the exploits required to release a userland jailbreak of iOS 5.1. It takes time to put them together in a public ready tool.
 Leave a comment, read comments [11]
Leave a comment, read comments [11]
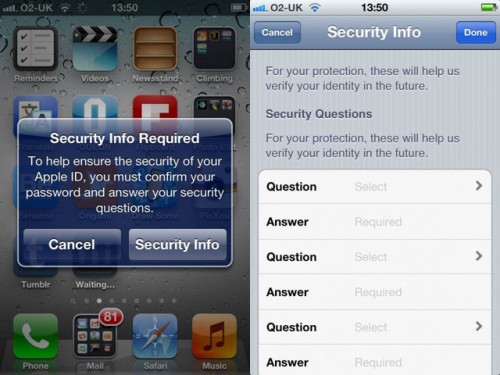
Apple improving iTunes account security with stricter requirements
Ars Technica reports that Apple has began asking users of iOS devices to select and answer some question related to their Apple IDs. Such measures were reportedly taken by the company to improve security of iTunes accounts.
After being shown the message, users are asked to select from a number of security questions and provide personal answers. Users are also prompted to provide a backup e-mail address in case the primary address associated with their Apple ID is compromised.
A Look Inside Apple Headquarters
The Apple Gazette has compiled a nice photo gallery that offers a look inside Apple Headquarters at 1 Infinite Loop. Take a look:
When you first walk inside Apple HQ, you’re greeted by the welcome/reception desk, which is situated inside the massive atrium with its bright natural light and suspended walkways.

Reception Desk

Apple HQ atrium
 Leave a comment, read comments [1]
Leave a comment, read comments [1]
Dropbox And Facebook iOS Apps Are Vulnerable To Credential Theft
This week Gareth Wright that Facebook's app for iOS has a security vulnerability through which malicious users can access login credentials saved in a .plist file of the app. With a copy of that .plist file malicious users could automatically log into the affected user's Facebook account on another device. Reportedly, the vulnerability also exists on Android devices.
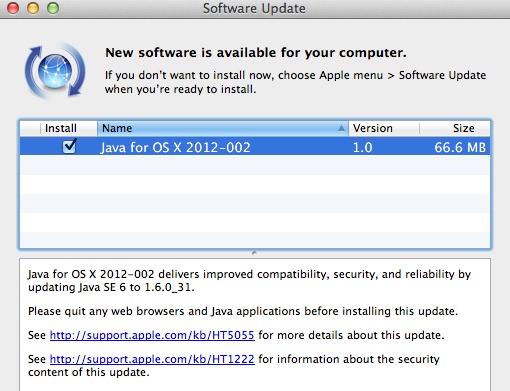
Apple Releases Its Second Java Update For OS X
Apple has released its second Java security update for OS X in two days. The first update closed Flashbaсk vulnerability that has affected 600,000 Macs.
RIM hiring iOS developers
Research in Motion has recently posted a job listing on its website that reveals that the BlackBerry maker is looking to hire developers for an undisclosed iOS enterprise app to be distributed through Apple's App Store. A RIM spokesperson confirmed the rumours. As he said, “the company is indeed developing an iPhone app as part of its BlackBerry Mobile Fusion project.”
Along with the usual coding and communication skills, requirements called for a candidate well-versed in creating apps for both the iPhone and the iPad.